Detect
Real-time detection involves utilizing detection tools to inform users of potential network anomalies that might indicate cyber security events. Real-time detection is meant to be a means to aid system operators in preventing a cyber event before it causes loss of equipment and safety. Real-time detection typically involves: utilizing monitoring and alerting tools to collect network data and events aggregating and processing events displaying events and potential vulnerabilities and notifying system users and operators of events
Key detection topics include:
- Real-Time Detection
- Network Scanning
- Security Information and Event Management
Real-Time Detection
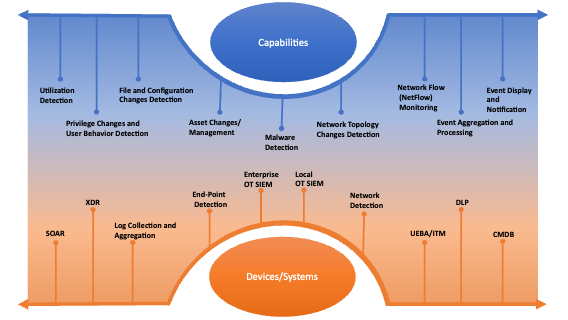
Real-time security monitoring and detection is a fundamental cyber security domain. It includes continuous monitoring of both digital assets from network-based and host-based sources to identify anomalies and threats in real-time. It minimizes the impact of cyber events on operations if an event were to occur and provides better knowledge of baseline operations. The real-time detection process includes Data Collection, Event Aggregation, Event Display and Notification, and Event Processing.
Challenges with real-time detection in power generation facilities include:
- Host-based detection capability is limited for native real-time equipment, such as programmable logic controllers and protective relays. Agent-based solutions are not typically compatible with these devices used in OT environments.
- Detection techniques, such as active interrogation of devices, may interfere with OT operation. OT compatibility and warranty concerns may limit deployment. This limits detection to mainly passive solutions.
Current real-time detection key practices include:
- Implemented through end-point detection, network-based detection, log collection and aggregation, and enterprise or OT security information and event management (SIEM) tools.
- Capabilities include multiple types of malicious activity detection (i.e., utilization, asset changes, file and configuration changes, malware, privilege, network flow, and topology) and event aggregation and processing.
- Common endpoint and network detection methods are well-established in OT systems.
- Cloud-based detection and third-party information-sharing tools were not prevalent in recent utility surveys.
Relevant EPRI Resources
- Real-Time Detection in Power Generation: Overview of Current State of Technology
- Automated Asset Discovery Performance Testing of Generation Sector Protocol Passive Network Traffic Capture Files
- Digital Twins – A Promising Technology for Data-Centric Cyber Security
- Distributed Control Systems, Automation Technologies, and Embedded Security: Generation Cybersecurity
- Industrial Control System Network Visibility Tool Use Cases
- Program on Technology Innovation: Integrated Security Operations Center and Monitoring and Diagnostics Digital Data Integration for Advanced Cyber-Physical Detection Capability—A Roadmap for the Energy Sector
Network Scanning
Scanning is critical to the generation plant cyber security strategy as it indicates network changes and software vulnerabilities. It can also identify gaps in hardening and segmentation.
Challenges with network scanning in power generation facilities include:
- Concerns about impacting operations limit active use scanning in OT networks.
- Scanning must be configured and implemented carefully in OT networks to ensure operations are not negatively impacted. This is typically performed during a maintenance or outage period.
Current scanning key practices include:
- Scanning tools utilize one or more of the following types of scanning: network discovery, host discovery, unauthorized or abnormal network activity, and vulnerabilities
- Passive Scanning: Passive scanning monitors network traffic by sniffing network traffic as it goes by and is less invasive than active scanning. Passive scanning only provides information for devices that do communicate through the monitoring point. Monitoring points are typically network TAPS or SPAN ports.
- Active Scanning: Active scanning tends to be more invasive as it actively sends packets to devices and can disrupt operations or cause device failures. Active scanning provides information for devices that can communicate across the scanning network range.
- Scanning software continues to converge both IT and OT by providing more comprehensive views of system devices, vulnerabilities, and potential behavior anomalies.
Relevant EPRI and Industry Resources
- Control System Protocols and Security Scanning: Guideline on Cyber Security Scanning for Generation Plant Control Systems
- Guideline on Cyber Security Scanning for Generation Plant Control Systems Computer Based Technology Transfer
- Industrial Control System Network Visibility Tool Use Cases
- CIP-005 R1.5, Electronic Security Perimeter
- CIP-007 R3.1, Malicious Software Prevention
- CIP-010 R2.1, Configuration Monitoring (High Impact BES Cyber Systems Only)
- CIP-010 R3.1, Vulnerability Assessments
Security Information and Event Management
Security information and event management (SIEM) becomes increasingly important as power generation operation technology becomes more digital and produces more alert information. SIEM solutions provide a means of identifying security events and enable near real-time detection capabilities across multiple environments. SIEM tools analyze aggregated security logs, system logs, and application logs from assets, which are then categorized into security events.
Challenges with security information and event management in power generation facilities include:
- Configuration and tuning is complex. Recent EPRI surveys indicate that many organizations receive and evaluate hundreds to thousands of false positives daily.
- As more IoT/IT/OT devices are incorporated into power systems, the data that is ingested by SIEM tools will increase in complexity and quantity. Data duplication further challenges tool deployment.
Current SIEM key practices include:
- Integration of IT and OT. Many tools are expanding to ingest data from a multitude of network monitoring tools and logging services to create a centralized place to evaluate vulnerabilities and network anomalies.
- Organizations are establishing consolidated SIEM solutions between IT and OT. OT dedicated SIEMs are commonly deployed, often in a dedicated Security Operations Center (SOC).
Relevant EPRI and industry Resources
- Security Event Monitoring Guideline: Generation Cyber Security
- Security Status Monitoring: Generation Cyber Security - Computer Based Technology Transfer
- Program on Technology Innovation: Integrated Security Operations Center and Monitoring and Diagnostics Digital Data Integration for Advanced Cyber-Physical Detection Capability—A Roadmap for the Energy Sector
- CIP-005-5 R1.1-R1.4, Identifying and Monitoring ESPs
- CIP-005-5 R1.5, Detecting and Documenting Malicious Communications
- CIP-007-6 R3, Malicious Code Prevention
- CIP-007-6 R4, Security Event Monitoring
- CIP-008-5 R2.3, Log Retention for Reportable Security Incidents
- CIP-010-2 R1 and R2, Configuration Management
- CIP-010-2 R3.1 and R3.2, Active Vulnerability Scanning
- CIP-011-2 R1, Cyber System Information Protection