Protect: Difference between revisions
No edit summary |
|||
| (21 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
==Protection Overview== | ==Protection Overview== | ||
Protection Summary | Protection Summary | ||
Protection is a cyber security focus area that addresses technology, methods, and best practices for protecting generation OT networks and digital equipment against cyber-attacks (e.g., hardening, encryption, identity and access management, etc.). The objective of protection is to prevent an attacker from gaining access or minimize the chance that it occurs. This includes identity and access management, data security, platform security, and the resiliency of the architecture and assets. Protective measures like hardening may also be implemented with existing tools. | |||
Key protection topics include: | '''Key protection topics''' include: | ||
*'''Security Architectures and Segmentation''' | *'''Security Architectures and Segmentation''' | ||
*'''Vulnerability Management''' | *'''Vulnerability Management''' | ||
| Line 11: | Line 12: | ||
== Segmentation and Security Architectures == | == Segmentation and Security Architectures == | ||
* [https://www.epri.com/research/programs/112046/results/3002027430 Defensible Network Architectures: Criteria for Secure OT Deployment in Power Systems] | |||
* [https://www.epri.com/research/programs/112046/results/3002011542 Connected Component Reference Architectures: Securing Connected Components in Power Generation—Interactive Remote Access, Vendor Use Case] | |||
* [https://www.epri.com/research/programs/112046/results/3002021184 Hydro Power DCS Upgrade Cyber Security Assessment: Cyber Security Technical Assessment Methodology (TAM) Case Study] | |||
* [https://www.epri.com/research/programs/112046/results/3002025919 Operational Technology (OT) Network Segmentation and Micro-Segmentation Strategies: An Evaluation of Segmentation Strategies in Generation Environments] | |||
* [https://www.epri.com/research/programs/112046/results/3002027431 Remote Access Jump Host Hardening Field Guide] | |||
* [https://www.epri.com/research/programs/112046/results/3002019308 Remote Centralization of Operations for Generation in Regard to Control, Instrumentation, and Protection Systems] | |||
* [https://www.epri.com/research/programs/112046/results/3002017149 SEL 487E Protective Relay Reference Cyber Security Data Sheet (CSDS): Cyber Security Technical Assessment Methodology Use Case Study] | |||
* [https://www.epri.com/research/programs/112046/results/3002019583 Zero Trust Considerations for Utility OT Cyber Security Strategies] | |||
== Vulnerability and Patch Management == | == Vulnerability and Patch Management == | ||
Vulnerability Management is an ongoing process of identifying, assessing and addressing security vulnerabilities. It involves the systematic discovery, assessment and remediation of vulnerabilities to reduce the risk of cyber attacks and data breaches. | Vulnerability Management is an ongoing process of identifying, assessing and addressing security vulnerabilities. It involves the systematic discovery, assessment and remediation of vulnerabilities to reduce the risk of cyber attacks and data breaches. | ||
'''Challenges''' with vulnerability and patch management in power generation facilities include: | '''Challenges''' with vulnerability and patch management in power generation facilities include: | ||
*Many | *Many companies utilize a manual process of identifying, prioritizing, and remediating vulnerabilities in OT systems. This process is time-consuming and error-prone. | ||
* | *Companies implement automated vulnerability scanning tools and threat intelligence feeds – prioritizing vulnerabilities based on their potential impact on operations. These tools typically require manual effort to review and disposition OT impact. | ||
*Dependencies on third | *Dependencies on third parties can introduce delays in the process of vulnerability remediation. Vendors validating the patches before the release can leave systems exposed for longer durations. To overcome this, a streamlined process should be established for validating and deploying the patches promptly. | ||
* | *Vulnerability advisories are not entirely accurate. In 2022 approximately 34% of vulnerabilities were found to be inaccurate. (Source: Dragos) | ||
*Adversaries interested in attacking old and unpatched vulnerabilities – The most exploited vulnerability of 2022 (Product - FortiOS and FortiProxy) was discovered in 2018 | *Adversaries interested in attacking old and unpatched vulnerabilities – The most exploited vulnerability of 2022 (Product - FortiOS and FortiProxy) was discovered in 2018 | ||
| Line 26: | Line 36: | ||
*Continuous Monitoring. Deploying automated tools to assess and monitor. Proper configuration and management of data should be done to avoid a significant backlog of data and alerts. | *Continuous Monitoring. Deploying automated tools to assess and monitor. Proper configuration and management of data should be done to avoid a significant backlog of data and alerts. | ||
*Automated Patch Deployment. Cautiously deploy automated tools using test environments, change management and rollback plans to avoid accidentally disrupting operations. | *Automated Patch Deployment. Cautiously deploy automated tools using test environments, change management, and rollback plans to avoid accidentally disrupting operations. | ||
*Vendor Support. Collaborate with vendors/suppliers to test and deploy patches | *Vendor Support. Collaborate with vendors/suppliers to test and deploy patches promptly. | ||
'''Relevant EPRI Resources''' | '''Relevant EPRI Resources''' | ||
*[https://www.epri.com/research/ | *[https://www.epri.com/research/programs/112046/results/3002024344 Risk-Informed Vulnerability and Patch Management Guide: Generation Cyber Security] | ||
* | *[https://www.epri.com/research/programs/112046/results/3002021170 Advanced Vulnerability Grading Tool (AVGT) v 1.1] | ||
* | *[https://www.epri.com/research/programs/112046/results/3002015258 Distributed Control Systems, Automation Technologies, and Embedded Security: Generation Cybersecurity] | ||
* | *[https://www.epri.com/research/programs/112046/results/3002014369 Control System Protocols and Security Scanning: Guideline on Cyber Security Scanning for Generation Plant Control Systems] | ||
*[https://www.epri.com/research/programs/112046/results/3002012752 Cyber Security Technical Assessment Methodology: Risk Informed Exploit Sequence Identification and Mitigation, Revision 1] | |||
*[https://www.epri.com/research/programs/112046/results/3002011188 Patch Management Guideline CBT Transfer Module, version 1.0] | |||
*[https://www.epri.com/research/programs/112046/results/3002011187 Patch Management Guidelines] | |||
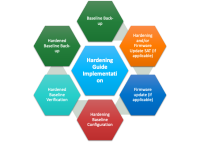
== Hardening == | == Hardening == | ||
Hardening is the process of securing systems and devices by reducing their attack surface and minimizing vulnerabilities. It involves configuring OT components with security best practices like limiting unnecessary access, disabling the ports and services not in use, and implementing strong authentication controls and encryption. | |||
'''Challenges''' with hardening in power generation facilities include: | |||
*Diverse & Legacy Systems makes it difficult to apply uniform hardening measures | |||
**Comprehensive asset inventory, prioritizing critical assets and gradually replacing legacy devices | |||
*Customized devices are not designed to handle traditional security configurations and can be too resource-intensive | |||
*Lightweight and critical controls should be implemented first. | |||
'''Current hardening key practices''' include vendor hardening, company-specific baselines, and asset configuration management: | |||
*Hardening is often performed during installation. Vendors typically have security hardening standards and images that are followed. | |||
*Address regulatory requirements, industry standards, and company-specific baselines. | |||
*Documentation asset configurations in conjunction with hardening. | |||
[[File:Hardening.png|200px|thumb|right|Hardening Implplementation]] | |||
'''Relevant EPRI Resources''' | |||
* [https://www.epri.com/research/programs/112046/results/3002018757 Generation Plant Equipment Cyber Security Hardening Field Guide: National Instruments cRIO Controller] | |||
* [https://www.epri.com/research/programs/112046/results/3002017095 Generation Plant Equipment Cyber Security Hardening Field Guide: Siemens S7 Controller] | |||
* [https://www.epri.com/research/programs/112046/results/3002017094 Generation Plant Equipment Cyber Security Hardening Field Guidebook] | |||
* [https://www.epri.com/research/programs/112046/results/3002021177 Generation Plant Equipment Cyber Security Hardening Guide: CompactLogix™ 5370-1769-L24ER-QB1B Programmable Automation Controller] | |||
* [https://www.epri.com/research/programs/112046/results/3002024343 Generation Plant Equipment Cyber Security Hardening, Field Guide: Allen Bradley Stratix 5700] | |||
* [https://www.epri.com/research/programs/112046/results/3002011904 Guideline on Digital I&C Configuration Management and Hardening for Generation Facilities] | |||
* [https://www.epri.com/research/programs/112046/results/3002011991 Guideline on Digital I&C Configuration Management and Hardening for Generation Facilities Computer Based Technology Transfer Module, version 1.0] | |||
* [https://www.epri.com/research/programs/112046/results/3002027431 Remote Access Jump Host Hardening Field Guide] | |||
* [https://www.epri.com/research/programs/112046/results/3002016128 Transient Cyber Assets (TCAs) and Removable Media Process Guidance: Generation Cyber Security] | |||
== Secure Remote Access == | == Secure Remote Access == | ||
| Line 42: | Line 81: | ||
== Identity and Access Management == | == Identity and Access Management == | ||
Identity and access management (IAM or IdAM) cyber security controls for authentication, authorization, and auditing only allow access when and where required to perform required operations. This includes verifying that the user is who they say they are. Identity and access management restricts unnecessary access and provides proper authentication and authorization methods for operation and maintenance. | |||
[[File:IAM.png|400px|thumb|right|IAM Capabilities, per EPRI Identity and Access Managment Guideline]] | |||
'''IAM Current Practices and Challenges''' in energy power generation: | |||
*Control systems utilize traditional methods such as Active Directory and local passwords. Multifactor authentication is implemented in some cases through IT/OT use cases, such as remote access through IT infrastructure. | |||
*Regulatory requirements for remote access users rely on coordinating notifications when roles change. | |||
*Password may eventually obsolete as passkeys and other forms of authentication seem to provide more security in verifying a human and/or device identity in a system. | |||
*The incorporation of cloud computing and digitalized assets, such as IoT devices and mobile devices, increases the need for more protection around understanding who a person is or what a device is and whether should it have access to perform a task. There has been an increase in phishing attacks leading to a greater need for protection beyond passwords. | |||
'''Relevant EPRI and Industry Resources''' | |||
*Security Management Controls, NERC CIP-003 standard, Version 9 | |||
*Personnel & Training, NERC CIP-004 standard, Version 7 | |||
*Electronic Security Perimeter(s), NERC CIP-005 standard, Version 7 | |||
*Physical Security of BES Cyber Systems, NERC CIP-006 standard, Version 6 | |||
*System Security Management, NERC CIP-007 standard, Version 6 | |||
*NIST Special Publication 1800-2, Identity and Access Management for Electric Utilities | |||
*NIST Special Publication 800-162, Guide to Attribute-Based Access Control (ABAC) Definition and Considerations | |||
'''Relevant EPRI and Industry Resources''' | |||
* [https://www.epri.com/research/programs/112046/results/3002014785 Access Control and Permission Management: Generation Cyber Security - Computer Based Technology Transfer] | |||
* [https://www.epri.com/research/programs/112046/results/3002027426 Identity and Access Management Guideline: Generation Cyber Security] | |||
*Security Management Controls, NERC CIP-003 standard, Version 9 | |||
*Personnel & Training, NERC CIP-004 standard, Version 7 | |||
*Electronic Security Perimeter(s), NERC CIP-005 standard, Version 7 | |||
*Physical Security of BES Cyber Systems, NERC CIP-006 standard, Version 6 | |||
*System Security Management, NERC CIP-007 standard, Version 6 | |||
*NIST Special Publication 1800-2, Identity and Access Management for Electric Utilities | |||
*NIST Special Publication 800-162, Guide to Attribute-Based Access Control (ABAC) Definition and Considerations | |||
Latest revision as of 19:23, 31 October 2024
Protection Overview
Protection Summary Protection is a cyber security focus area that addresses technology, methods, and best practices for protecting generation OT networks and digital equipment against cyber-attacks (e.g., hardening, encryption, identity and access management, etc.). The objective of protection is to prevent an attacker from gaining access or minimize the chance that it occurs. This includes identity and access management, data security, platform security, and the resiliency of the architecture and assets. Protective measures like hardening may also be implemented with existing tools.
Key protection topics include:
- Security Architectures and Segmentation
- Vulnerability Management
- Hardening
- Secure Remote Access
- Transient Cyber Assets and Removable Media
- Identity and Access Management
Segmentation and Security Architectures
- Defensible Network Architectures: Criteria for Secure OT Deployment in Power Systems
- Connected Component Reference Architectures: Securing Connected Components in Power Generation—Interactive Remote Access, Vendor Use Case
- Hydro Power DCS Upgrade Cyber Security Assessment: Cyber Security Technical Assessment Methodology (TAM) Case Study
- Operational Technology (OT) Network Segmentation and Micro-Segmentation Strategies: An Evaluation of Segmentation Strategies in Generation Environments
- Remote Access Jump Host Hardening Field Guide
- Remote Centralization of Operations for Generation in Regard to Control, Instrumentation, and Protection Systems
- SEL 487E Protective Relay Reference Cyber Security Data Sheet (CSDS): Cyber Security Technical Assessment Methodology Use Case Study
- Zero Trust Considerations for Utility OT Cyber Security Strategies
Vulnerability and Patch Management
Vulnerability Management is an ongoing process of identifying, assessing and addressing security vulnerabilities. It involves the systematic discovery, assessment and remediation of vulnerabilities to reduce the risk of cyber attacks and data breaches.
Challenges with vulnerability and patch management in power generation facilities include:
- Many companies utilize a manual process of identifying, prioritizing, and remediating vulnerabilities in OT systems. This process is time-consuming and error-prone.
- Companies implement automated vulnerability scanning tools and threat intelligence feeds – prioritizing vulnerabilities based on their potential impact on operations. These tools typically require manual effort to review and disposition OT impact.
- Dependencies on third parties can introduce delays in the process of vulnerability remediation. Vendors validating the patches before the release can leave systems exposed for longer durations. To overcome this, a streamlined process should be established for validating and deploying the patches promptly.
- Vulnerability advisories are not entirely accurate. In 2022 approximately 34% of vulnerabilities were found to be inaccurate. (Source: Dragos)
- Adversaries interested in attacking old and unpatched vulnerabilities – The most exploited vulnerability of 2022 (Product - FortiOS and FortiProxy) was discovered in 2018
Current vulnerability and patch management key practices include continuous monitoring, automated patch deployment, and vendor patch support and outsourcing:
- Continuous Monitoring. Deploying automated tools to assess and monitor. Proper configuration and management of data should be done to avoid a significant backlog of data and alerts.
- Automated Patch Deployment. Cautiously deploy automated tools using test environments, change management, and rollback plans to avoid accidentally disrupting operations.
- Vendor Support. Collaborate with vendors/suppliers to test and deploy patches promptly.
Relevant EPRI Resources
- Risk-Informed Vulnerability and Patch Management Guide: Generation Cyber Security
- Advanced Vulnerability Grading Tool (AVGT) v 1.1
- Distributed Control Systems, Automation Technologies, and Embedded Security: Generation Cybersecurity
- Control System Protocols and Security Scanning: Guideline on Cyber Security Scanning for Generation Plant Control Systems
- Cyber Security Technical Assessment Methodology: Risk Informed Exploit Sequence Identification and Mitigation, Revision 1
- Patch Management Guideline CBT Transfer Module, version 1.0
- Patch Management Guidelines
Hardening
Hardening is the process of securing systems and devices by reducing their attack surface and minimizing vulnerabilities. It involves configuring OT components with security best practices like limiting unnecessary access, disabling the ports and services not in use, and implementing strong authentication controls and encryption.
Challenges with hardening in power generation facilities include:
- Diverse & Legacy Systems makes it difficult to apply uniform hardening measures
- Comprehensive asset inventory, prioritizing critical assets and gradually replacing legacy devices
- Customized devices are not designed to handle traditional security configurations and can be too resource-intensive
- Lightweight and critical controls should be implemented first.
Current hardening key practices include vendor hardening, company-specific baselines, and asset configuration management:
- Hardening is often performed during installation. Vendors typically have security hardening standards and images that are followed.
- Address regulatory requirements, industry standards, and company-specific baselines.
- Documentation asset configurations in conjunction with hardening.
Relevant EPRI Resources
- Generation Plant Equipment Cyber Security Hardening Field Guide: National Instruments cRIO Controller
- Generation Plant Equipment Cyber Security Hardening Field Guide: Siemens S7 Controller
- Generation Plant Equipment Cyber Security Hardening Field Guidebook
- Generation Plant Equipment Cyber Security Hardening Guide: CompactLogix™ 5370-1769-L24ER-QB1B Programmable Automation Controller
- Generation Plant Equipment Cyber Security Hardening, Field Guide: Allen Bradley Stratix 5700
- Guideline on Digital I&C Configuration Management and Hardening for Generation Facilities
- Guideline on Digital I&C Configuration Management and Hardening for Generation Facilities Computer Based Technology Transfer Module, version 1.0
- Remote Access Jump Host Hardening Field Guide
- Transient Cyber Assets (TCAs) and Removable Media Process Guidance: Generation Cyber Security
Secure Remote Access
Transient Cyber Assets and Removeable Media
Identity and Access Management
Identity and access management (IAM or IdAM) cyber security controls for authentication, authorization, and auditing only allow access when and where required to perform required operations. This includes verifying that the user is who they say they are. Identity and access management restricts unnecessary access and provides proper authentication and authorization methods for operation and maintenance.
IAM Current Practices and Challenges in energy power generation:
- Control systems utilize traditional methods such as Active Directory and local passwords. Multifactor authentication is implemented in some cases through IT/OT use cases, such as remote access through IT infrastructure.
- Regulatory requirements for remote access users rely on coordinating notifications when roles change.
- Password may eventually obsolete as passkeys and other forms of authentication seem to provide more security in verifying a human and/or device identity in a system.
- The incorporation of cloud computing and digitalized assets, such as IoT devices and mobile devices, increases the need for more protection around understanding who a person is or what a device is and whether should it have access to perform a task. There has been an increase in phishing attacks leading to a greater need for protection beyond passwords.
Relevant EPRI and Industry Resources
- Security Management Controls, NERC CIP-003 standard, Version 9
- Personnel & Training, NERC CIP-004 standard, Version 7
- Electronic Security Perimeter(s), NERC CIP-005 standard, Version 7
- Physical Security of BES Cyber Systems, NERC CIP-006 standard, Version 6
- System Security Management, NERC CIP-007 standard, Version 6
- NIST Special Publication 1800-2, Identity and Access Management for Electric Utilities
- NIST Special Publication 800-162, Guide to Attribute-Based Access Control (ABAC) Definition and Considerations
Relevant EPRI and Industry Resources
- Access Control and Permission Management: Generation Cyber Security - Computer Based Technology Transfer
- Identity and Access Management Guideline: Generation Cyber Security
- Security Management Controls, NERC CIP-003 standard, Version 9
- Personnel & Training, NERC CIP-004 standard, Version 7
- Electronic Security Perimeter(s), NERC CIP-005 standard, Version 7
- Physical Security of BES Cyber Systems, NERC CIP-006 standard, Version 6
- System Security Management, NERC CIP-007 standard, Version 6
- NIST Special Publication 1800-2, Identity and Access Management for Electric Utilities
- NIST Special Publication 800-162, Guide to Attribute-Based Access Control (ABAC) Definition and Considerations